Virtual Private Cloud (VPC)
Provision a logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define.
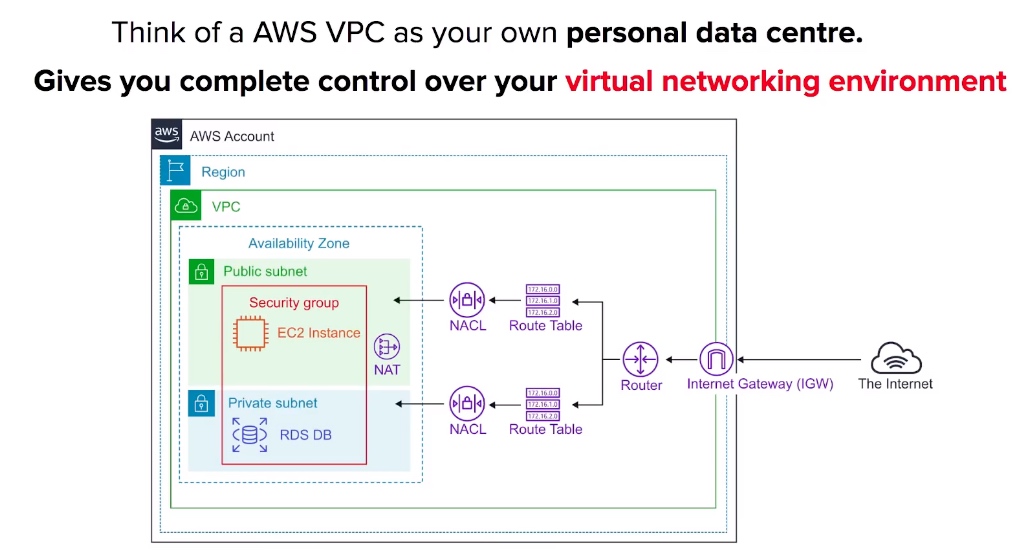
Core Components

Key Features
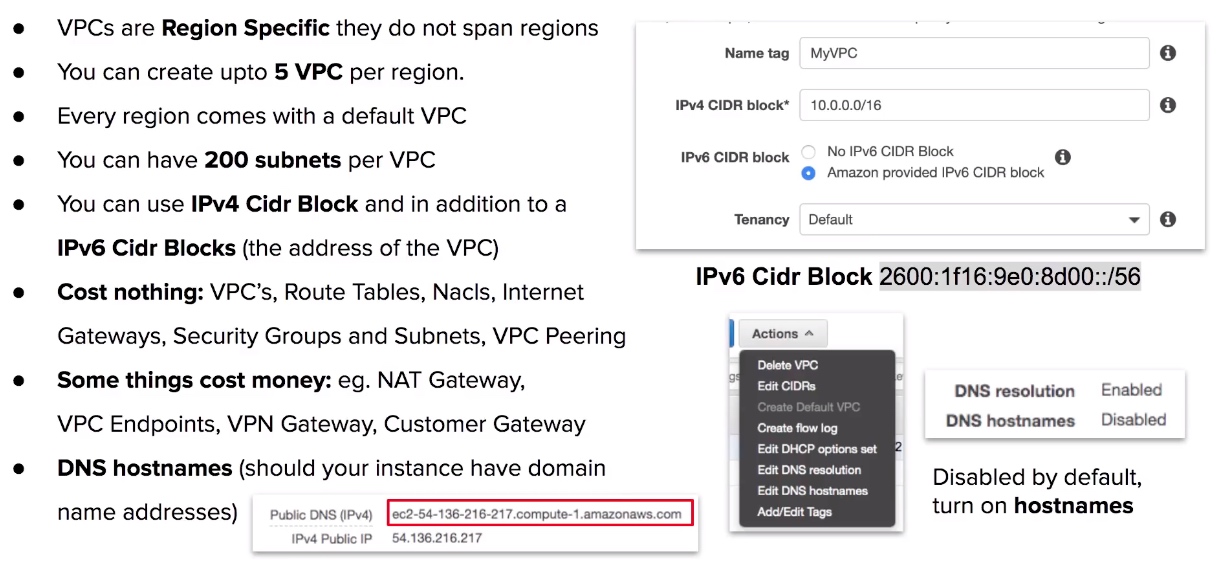
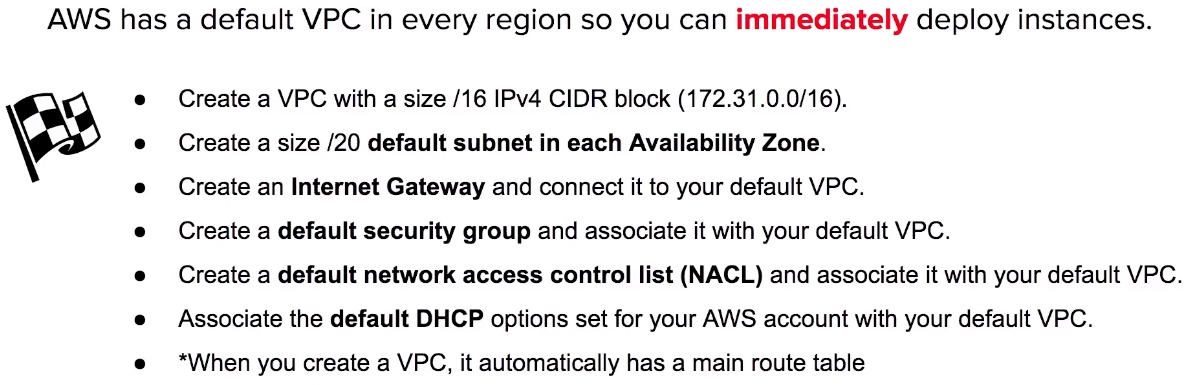
Default VPC
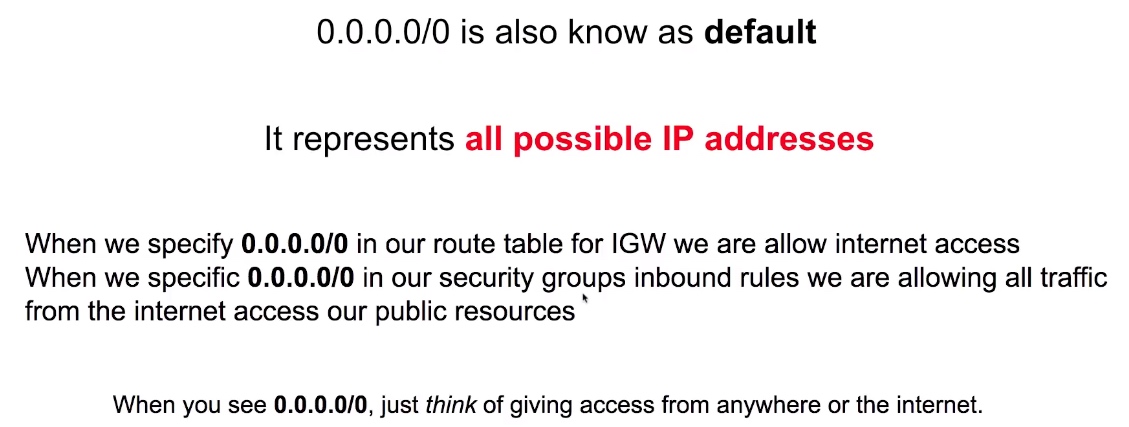
0.0.0.0/0
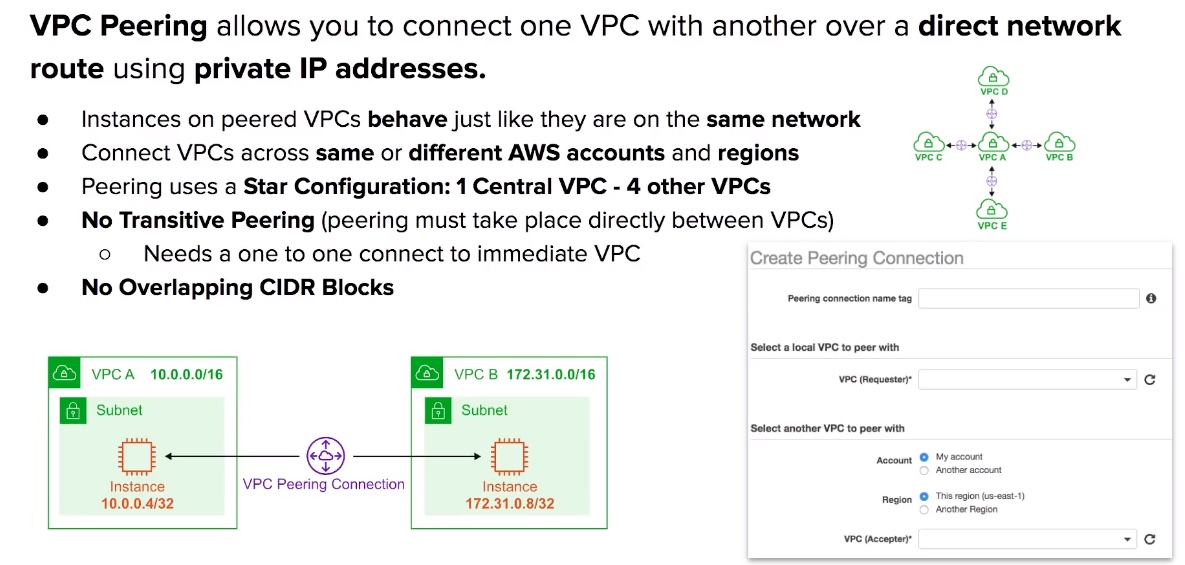
VPC Peering
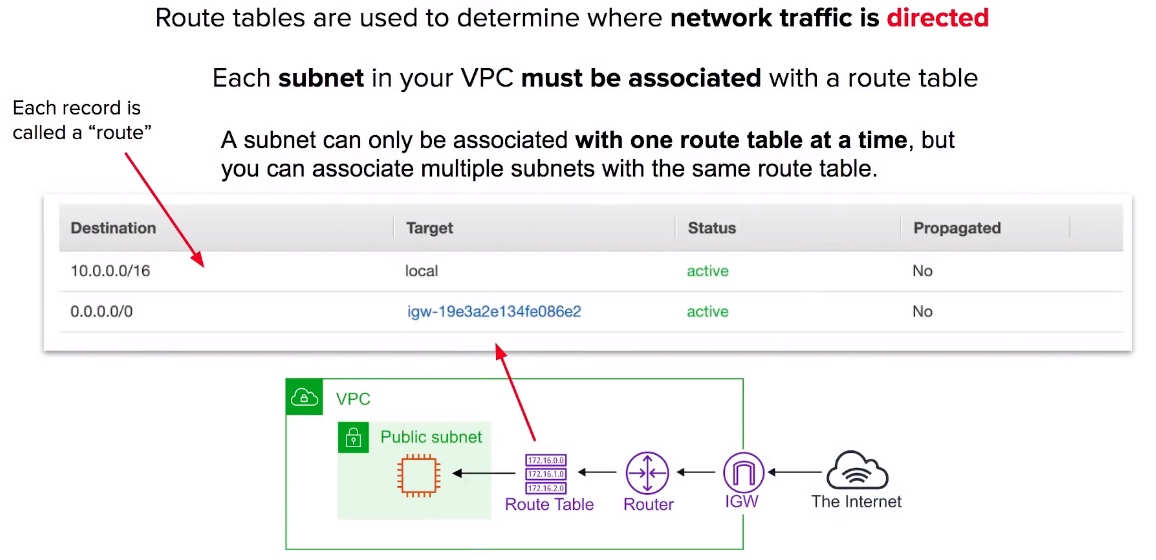
Route Tables
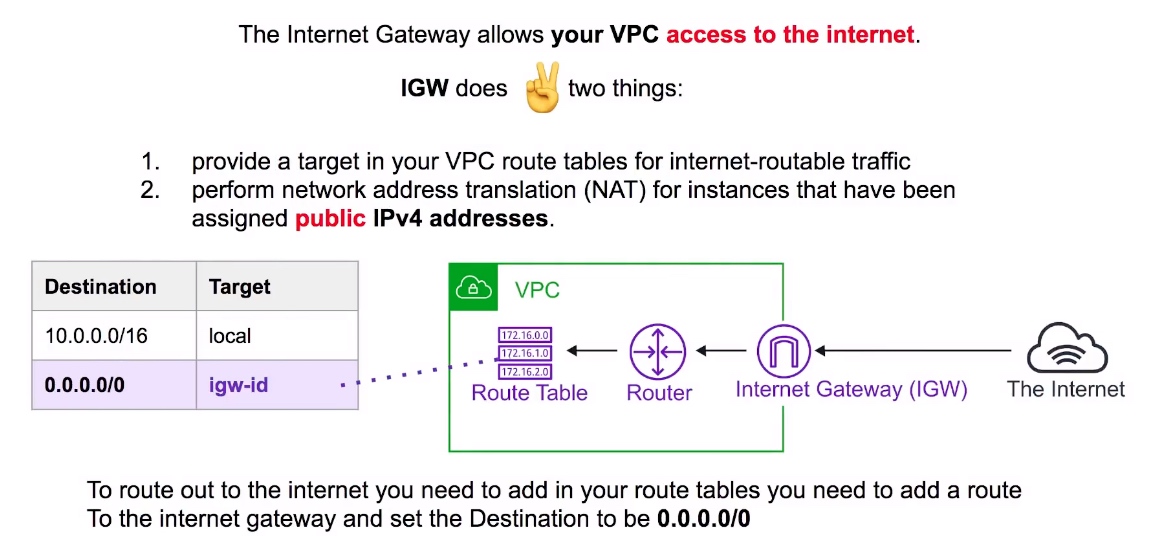
Internet Gateway (IGW)
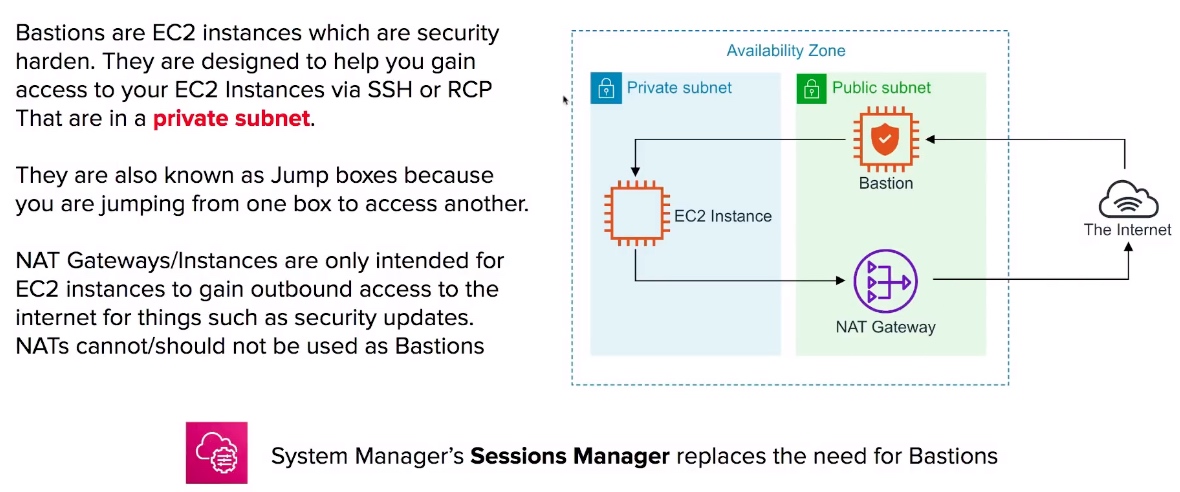
Basiton/Jumpbox
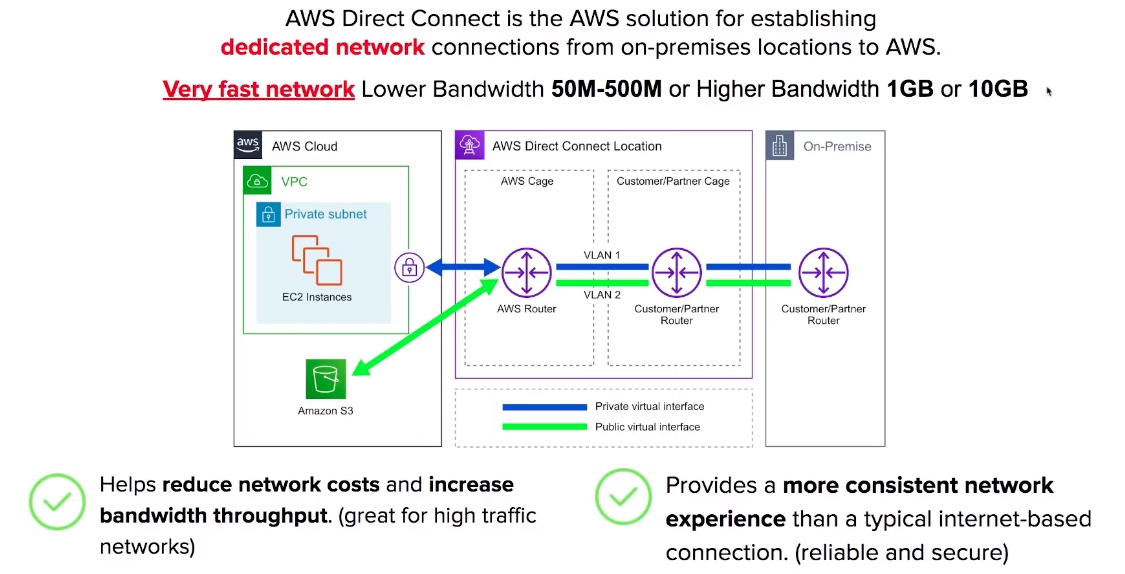
Direct Connect
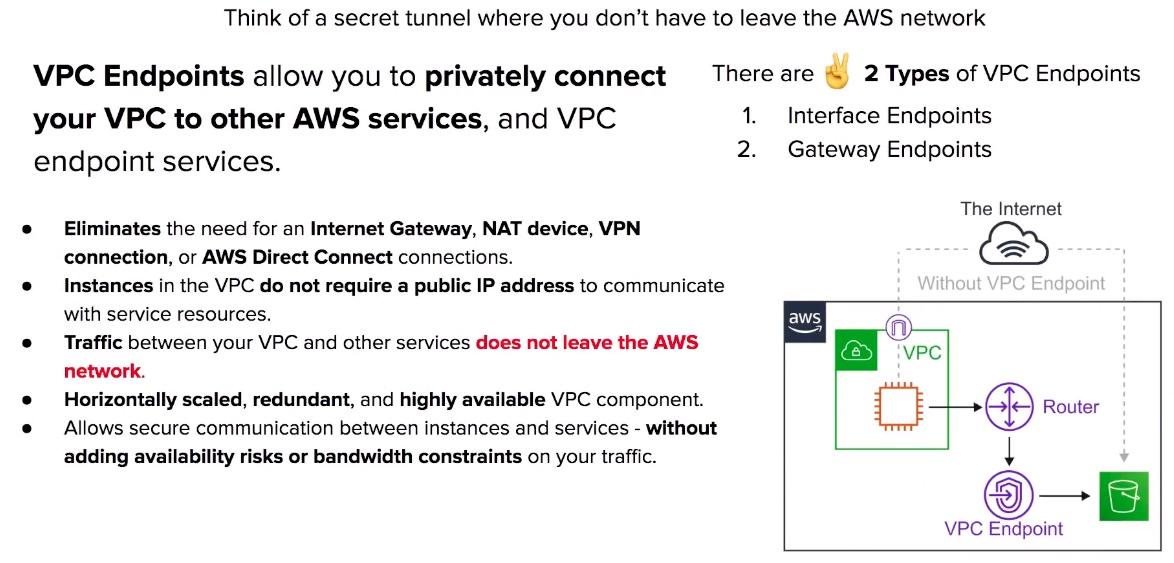
VPC Endpoints
Interface Endpoints

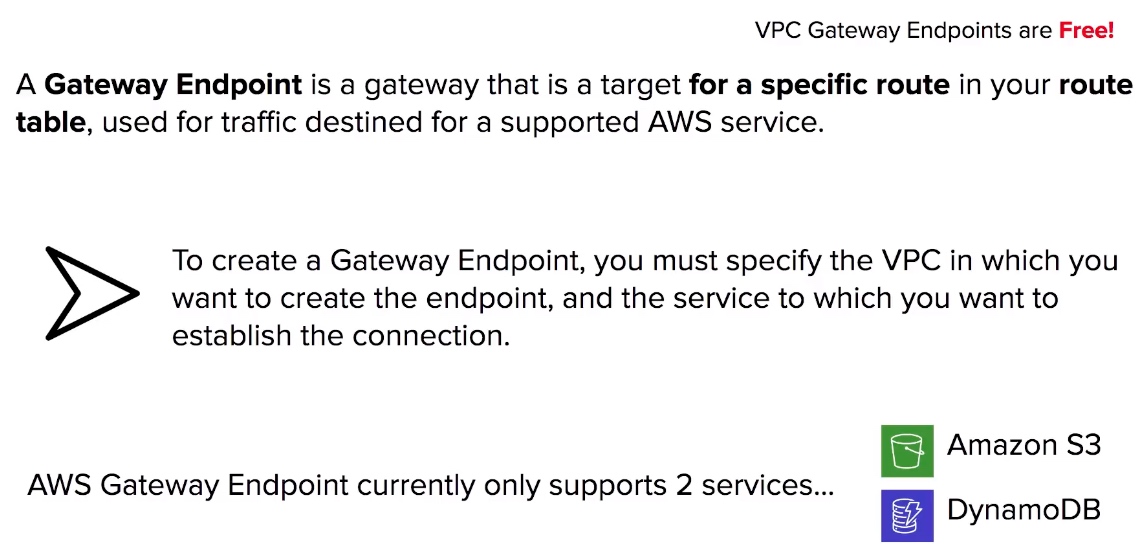
VPC Gateway Endpoints
VPC Endpoint CheatSheet
- VPC Endpoints help keep traffic between AWS services within the AWS Network.
- There are two kinds of VPC Endpoints. Interface Endpoints and Gateway Endpoints.
- Interface Endpoints cost money, Gateway Endpoints are free.
- Interface Endpoints uses an Elastic Network Interface (ENI) with Private IP (powered by AWS PrivateLink).
- Gateway Endpoints is a target for a specific route in your route table.
- Interface Endpoints support many AWS services.
- Gateway Endpoint only supports DynamoDB and S3.
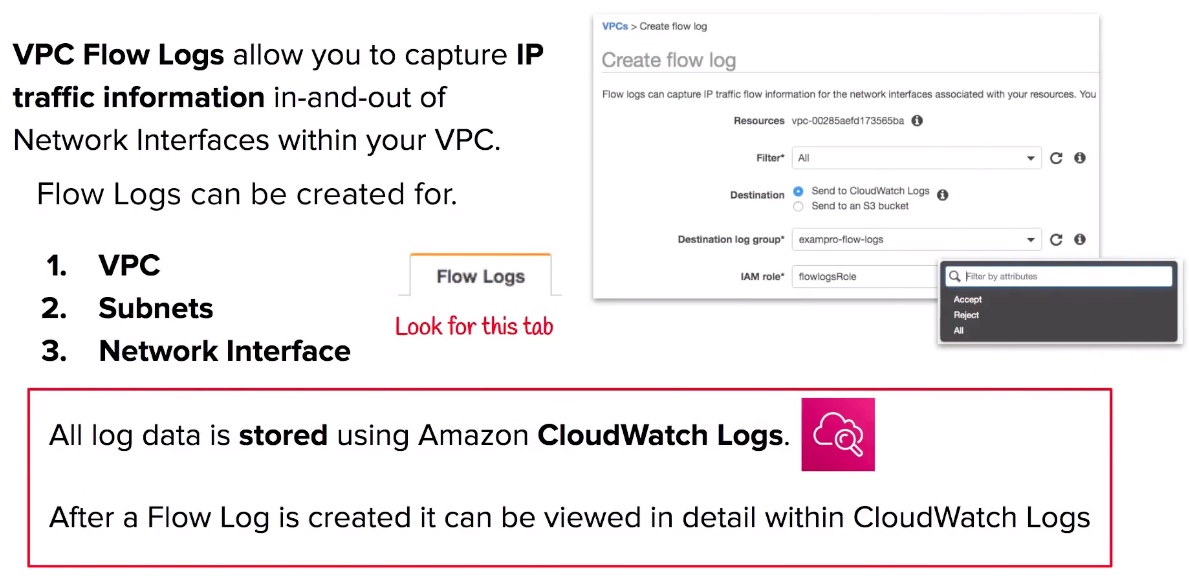
VPC Flow Logs
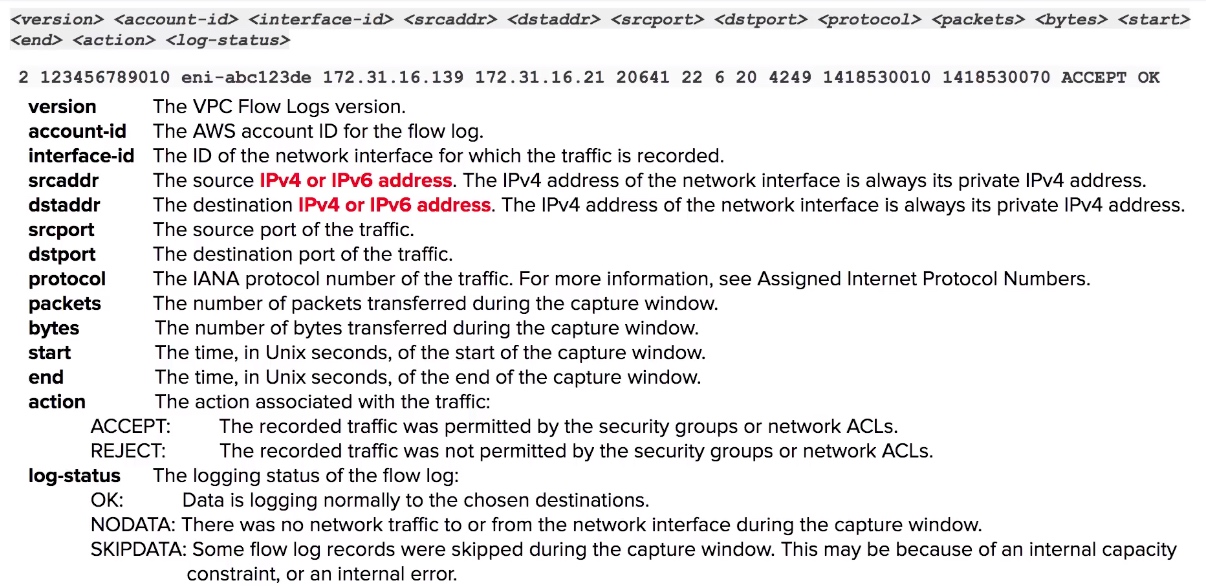
CheatSheet
- VPC Flow Logs monitor the in-and-out traffic of your Network Interfaces within your VPC.
- You can turn on Flow Logs at the VPC, Subnet or Network Interface level.
- VPC Flow Logs cannot be tagged like other AWS resources.
- You cannot change the configuration of a flow log after it’s created.
- You cannot enable flow logs for VPCs which are peered with your VPC unless it is in the same account.
- VPC Flow Logs can be delivered to an S3 or CloudWatch Logs.
- VPC Flow Logs contains the source and destination IP addresses (not hostnames)
- Some instance traffic is not monitored:
- Instance traffic generated by contacting the AWS DNS servers
- Windows license activation traffic from instances
- Traffic to and from the instance metadata address (169.254.169.254)
- DHCP Traffic
- Any traffic to the reserved IP address of the default VPC router
Network Access Control List (NACL)
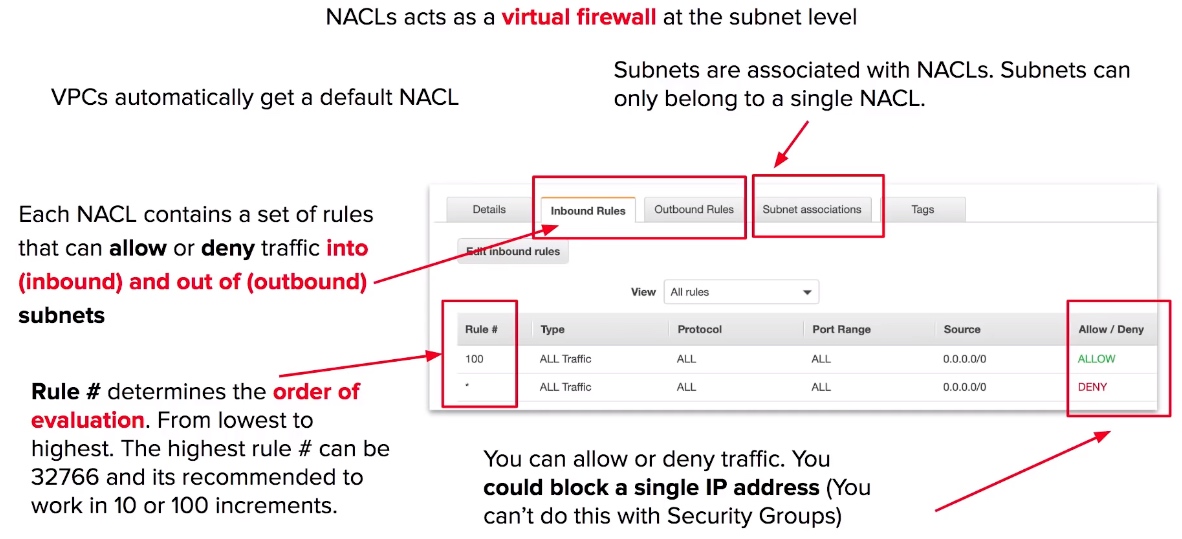
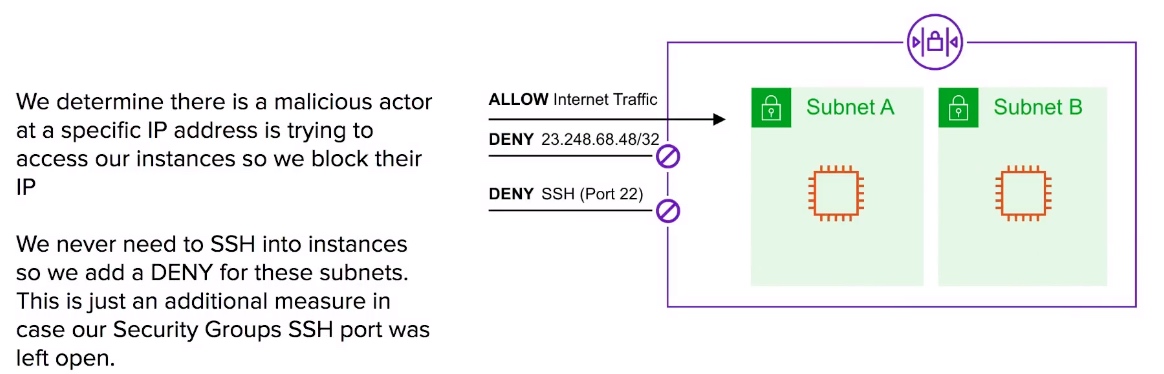
NACLs Use Case
NACLs CheatSheet
- Network Access Control List is commonly known as NACL.
- VPCs are automatically given a default NACL which allows all outbound and inbound traffic.
- Each subnet within a VPC must be associated with a NACL.
- Subnets can only be associated with 1 NACL at a time. Associating a subnet with a new NACL will remove the previous association.
- If a NACL is not explicitly associated with a subnet, the subnet will automatically be associated with the default NACL.
- NACL has inbound and outbound rules (just like Security Groups).
- Rule can either allow or deny traffic. (unlike Security Groups which can only allow)
- NACLs are STATELESS
(any allowed inbound traffic is also allowed outbound) - When you create a NACLs it will deny all traffic by default.
- NACLs contain a numbered list of rules that get evaluated in order from lowest to highest.
- If you needed to block a single IP address you could via NACLs. (Security Groups cannot deny)
Security Groups
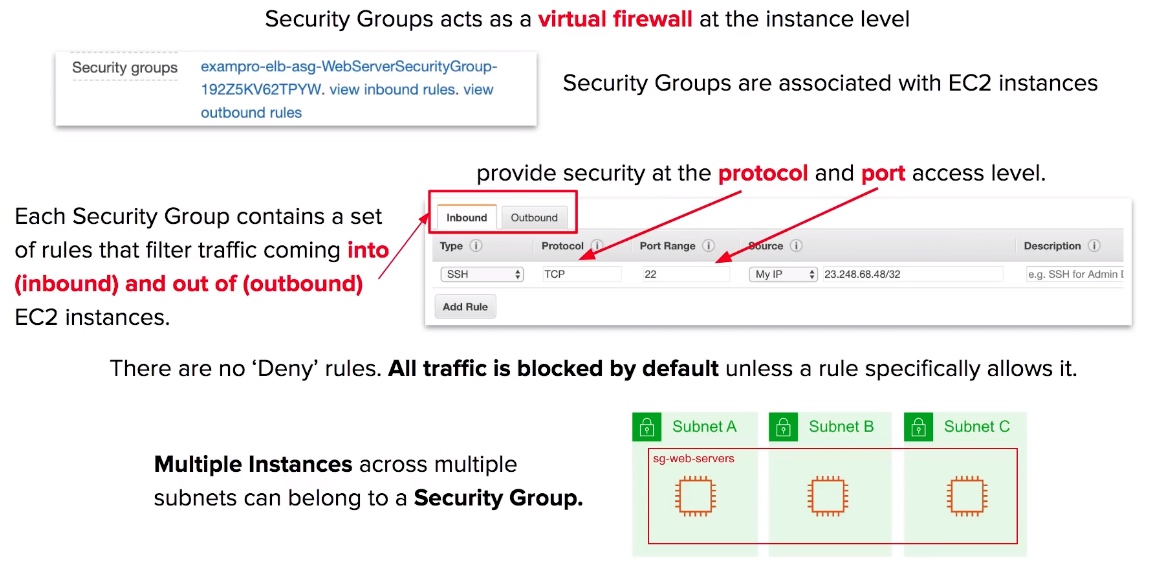
Security Group Use case
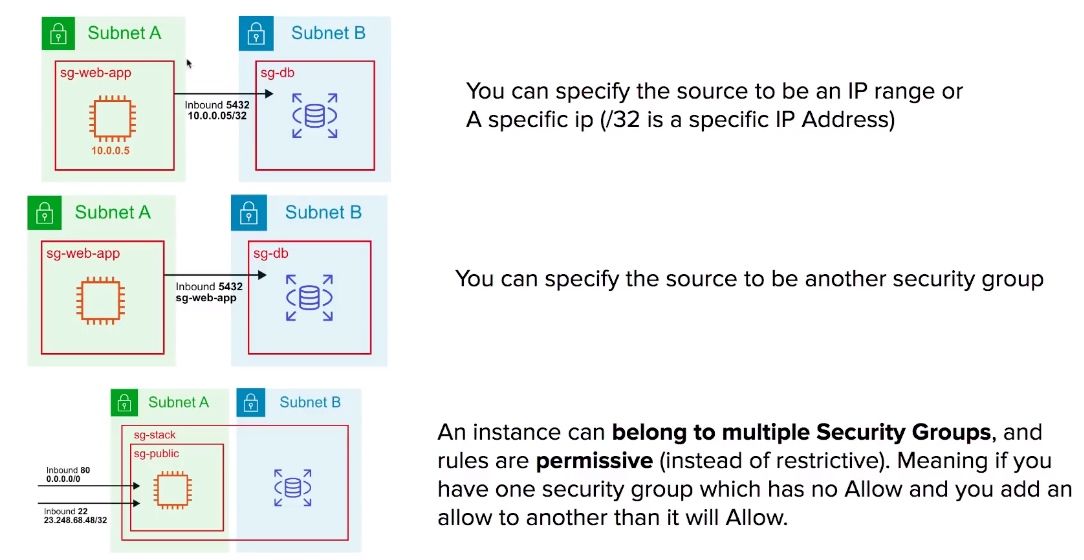
Security Group CheatSheet
- Security Groups act as a firewall at the instance level.
- Unless allowed specifically, all inbound traffic is blocked by default.
- All Outbound traffic from the instance is allowed by default.
- You can specific for the source to be either an IP range, single Ip Address or another security group.
- Security Groups are STATEFUL
(if traffic is allowed inbound it is also allowed outbound). Note: stateful firewall tracks the operating state and characteristics of network connections traversing it, such as TCP stages. - Any changes to a Security Group take effect immediately.
- EC2 Instances can belong to multiple security groups.
- Security groups can contain multiple EC2 Instances.
- You cannot block specific IP addresses with Security Groups (only allow rules), for this you would need a Network Access Control List (NACL) to deny IP addresses.
- You can have upto 10,000 Security Groups per Region. (default 2,5000)
- You can have 60 inbound and 60 outbound rules pre Security Group.
- You can have 16 Security Groups associated to an ENI (default is 5).
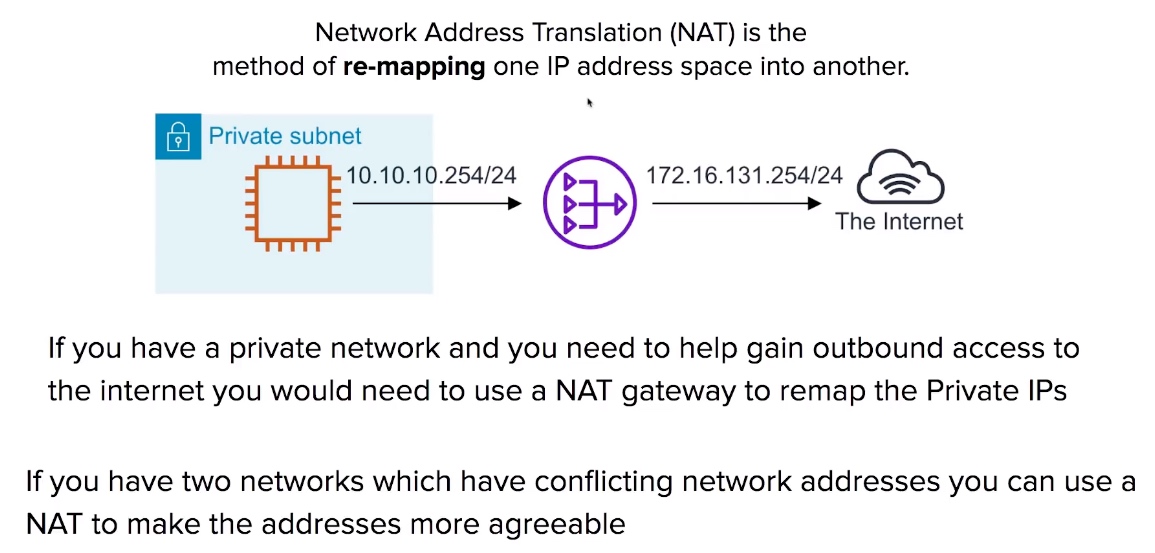
Network Address Translation (NAT)
NAT Instances vs NAT Gateways
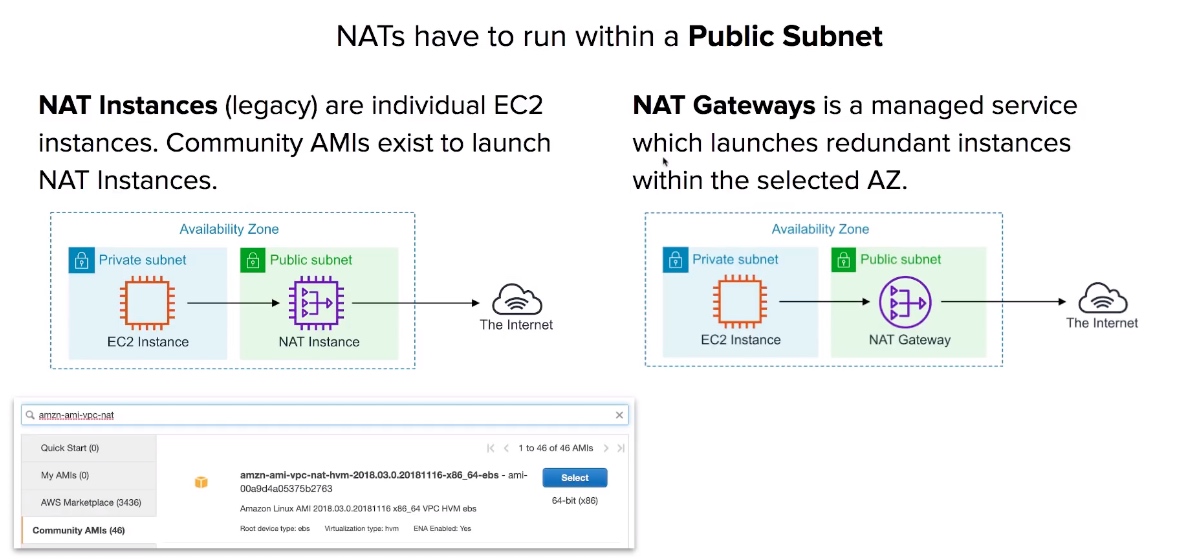
NAT Instance and NAT Gateway CheatSheet
NAT Instance:
- When creating a NAT instance you must disable source and destination checks on the instance.
- NAT instances must exist in a public subnet.
- You must have a route out of the private subnet to the NAT instance.
- The size of a NAT instance determines how much traffic can be handled.
- High availability can be achieved using Autoscaling Groups, multiple subnets in different AZs, and automate failover between them using a script.
NAT Gateway:
- NAT Gateways are redundant inside an Availability Zone. (can survive failure of EC2 instance)
- You can only have 1 NAT Gateway inside 1 Availability Zone. (cannot span AZs)
- Starts at 5 Gbps and scales all the way up to 45 Gbps.
- NAT Gateways are the preferred setup for enterprise systems.
- There is no requirement to patch NAT Gateways, and there is no need to disable Source/Destination checks for the NAT Gateway. (unlike NAT Instances)
- NAT Gateways are automatically assigned a public IP address.
- Route Tables for the NAT Gateway MUST be updated.
- Resources in multiple AZs sharing a Gateway will lose internet access if the Gateway goes down, unless you create a Gateway in each AZ and configure route tables accordingly.