Identity and Access Management (IAM)
Manages access of AWS users and resources
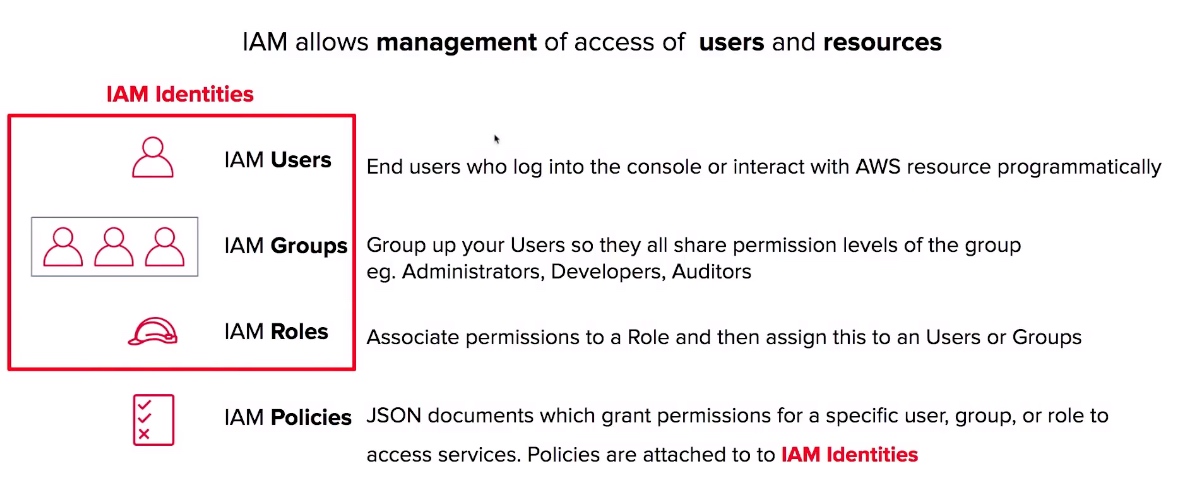
IAM Core Components
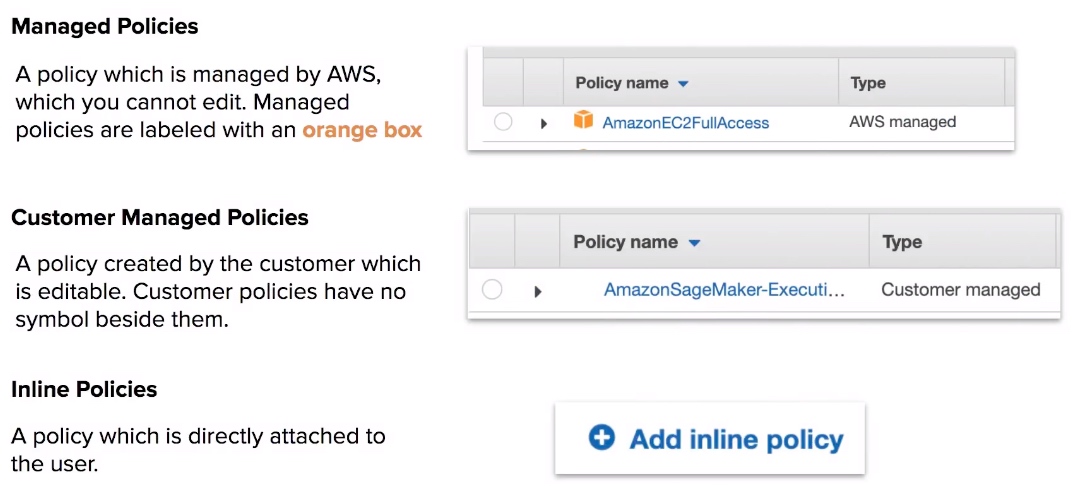
Types of Policies
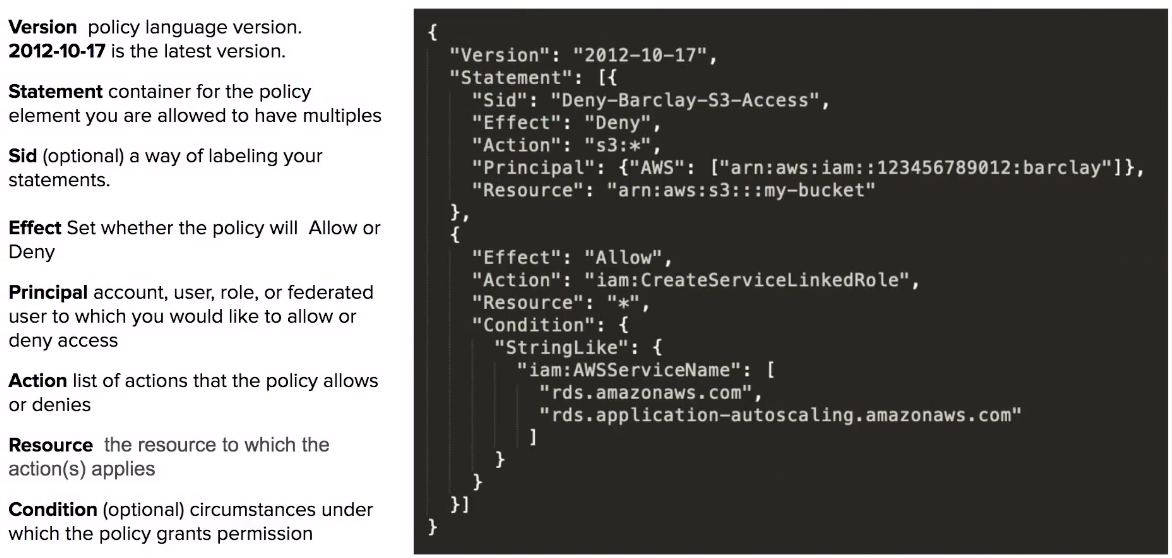
Policy Structure
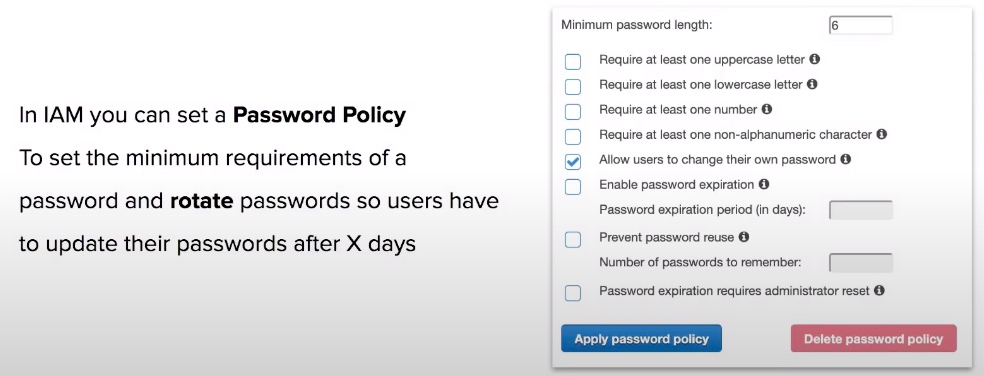
Password Policy
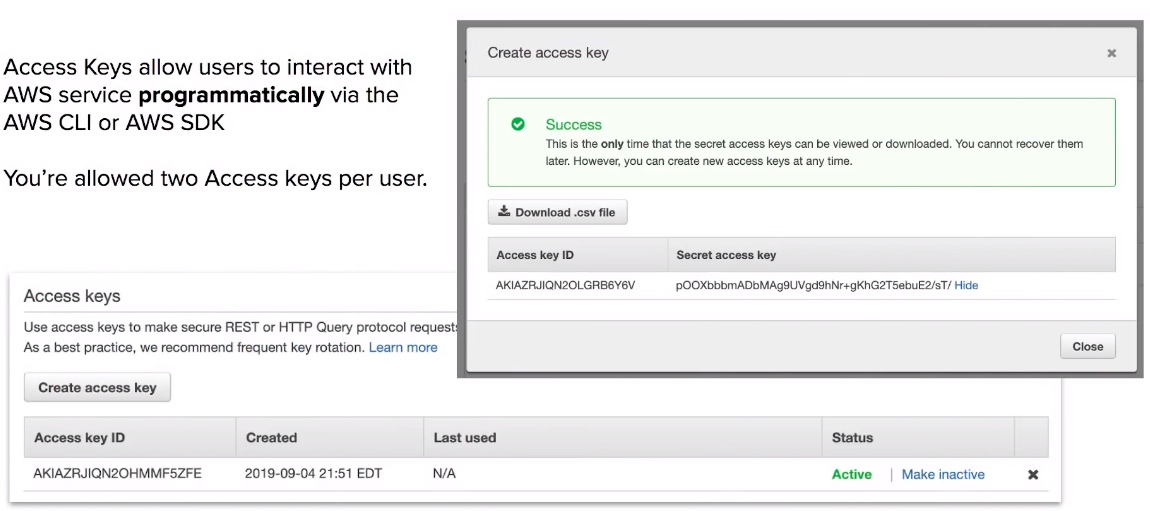
Programmatic Access Keys
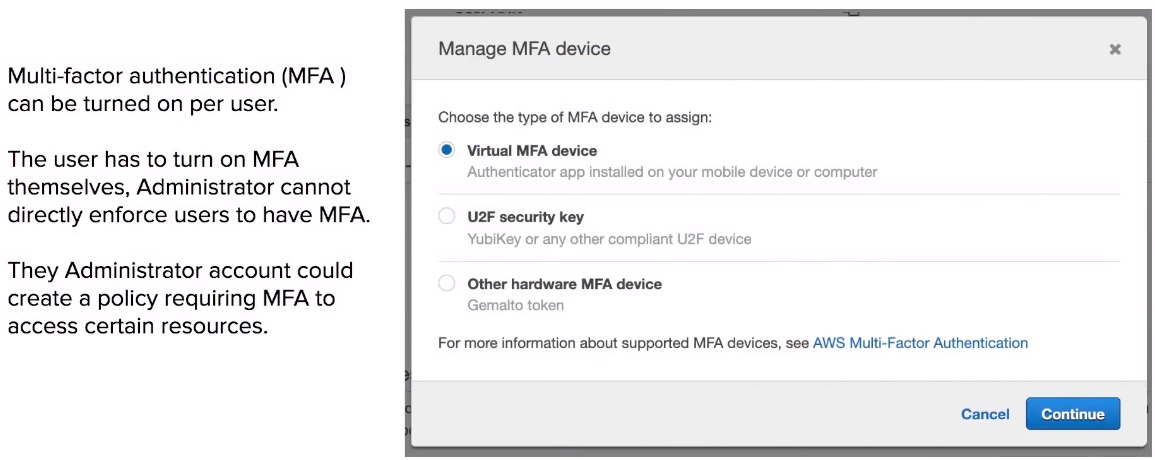
Multi-Factor Authentication (MFA)
IAM CheatSheet
- Identity Access Management is used to manage access to users and resources.
- IAM is a universal system. (applied to all regions at the same time). IAM is a free service.
- A root account is the account initially created when AWS is set up. (full administrator)
- New IAM accounts have no permissions by default until granted.
- New users get assigned an Access Key ld and Secret when first created when you give them programmatic access.
- Access Keys are only used for CLI and SDK. (cannot access console)
- Access keys are only shown once when created. If lost they must be deleted/recreated again.
- Always setup MFA for Root Accounts.
- Users must enable MFA on their own, Administrator cannot turn it on for each user.
- IAM allows your set password policies to set minimum password requirements or rotate passwords.
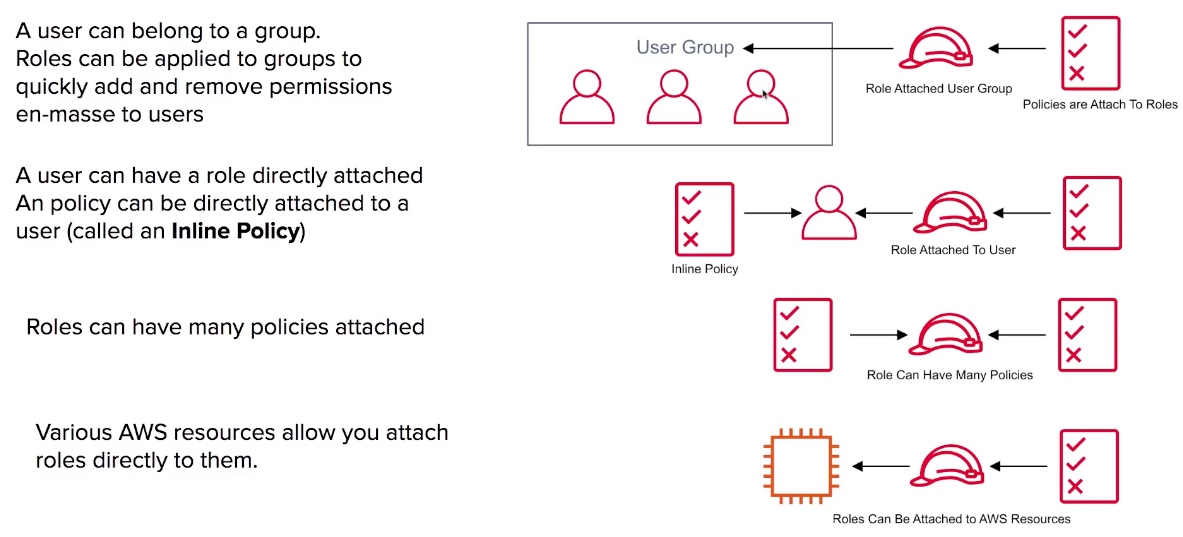
- IAM Identities as Users, Groups, and Roles.
- IAM Users End users who log into the console or interact with AWS resources programmatically.
- IAM Groups Group up your Users so they all share permission levels of the group. eg. Administrators, Developers, Auditors
- IAM Roles Associate permissions to a Role and then assign this to an Users or Groups.
- IAM Policies JSON documents which grant permissions for a specific user, group, or role to access services. Policies are attached to to IAM Identities.
- Managed Policies are policies provided by AWS and cannot be edited.
- Customer Managed Policies are policies created by use the customer, which you can edit.
- Inline Policies are policies which are directly attached to a user.
Amazon Cognito
Decentralized Managed Authentication. Sign-up, sign-in integration for your apps. Social identity provider(abbreviated IdP or IDP) eg. Facebook, Google.
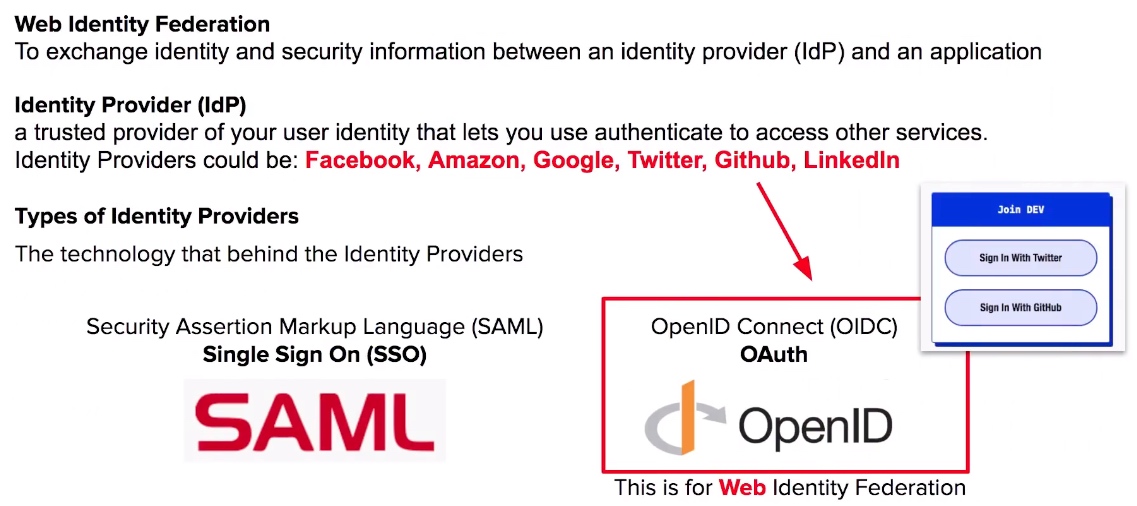
Web Identity Federation and Identity Provider
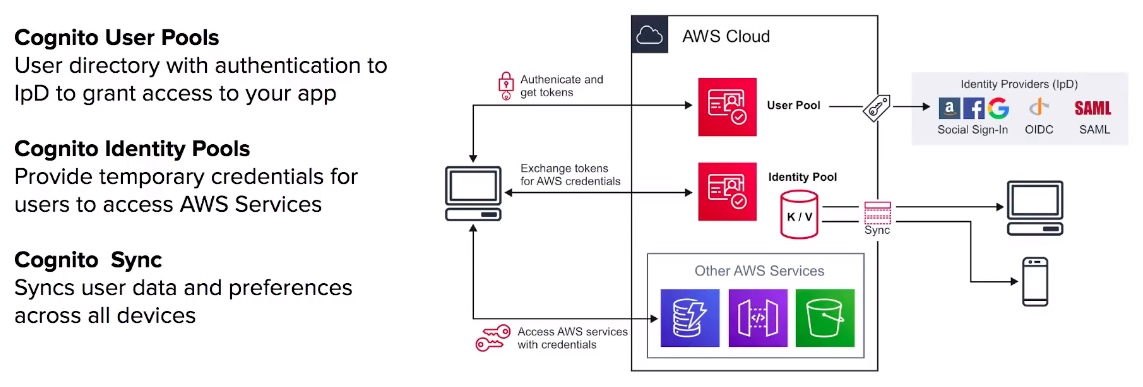
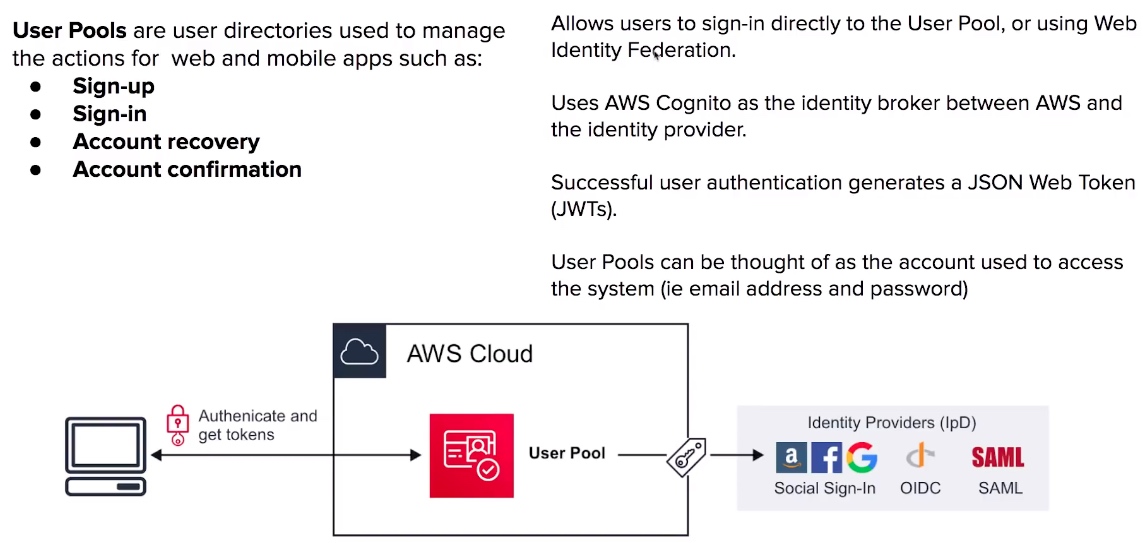
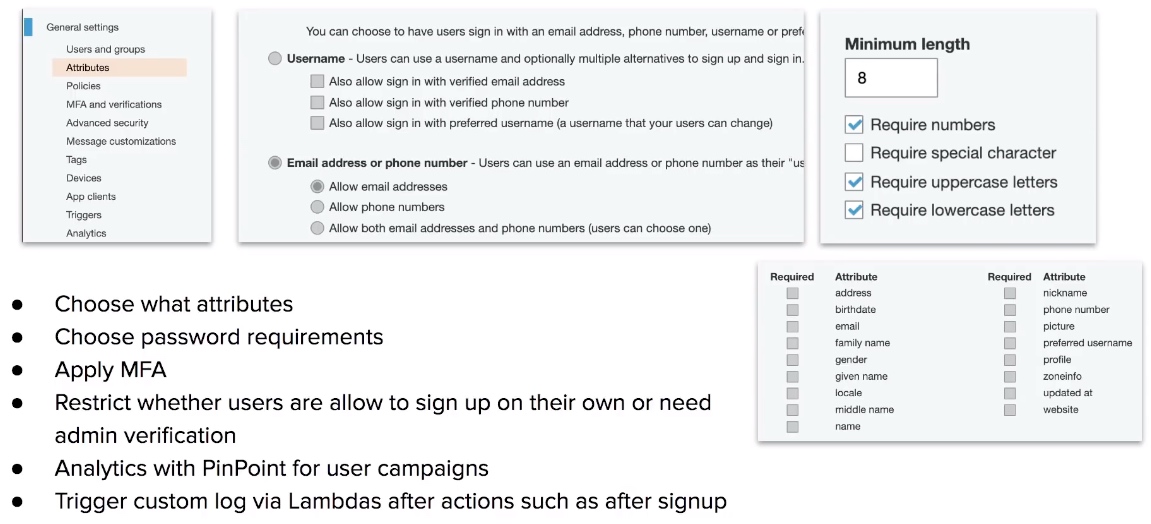
Cognito User Pools
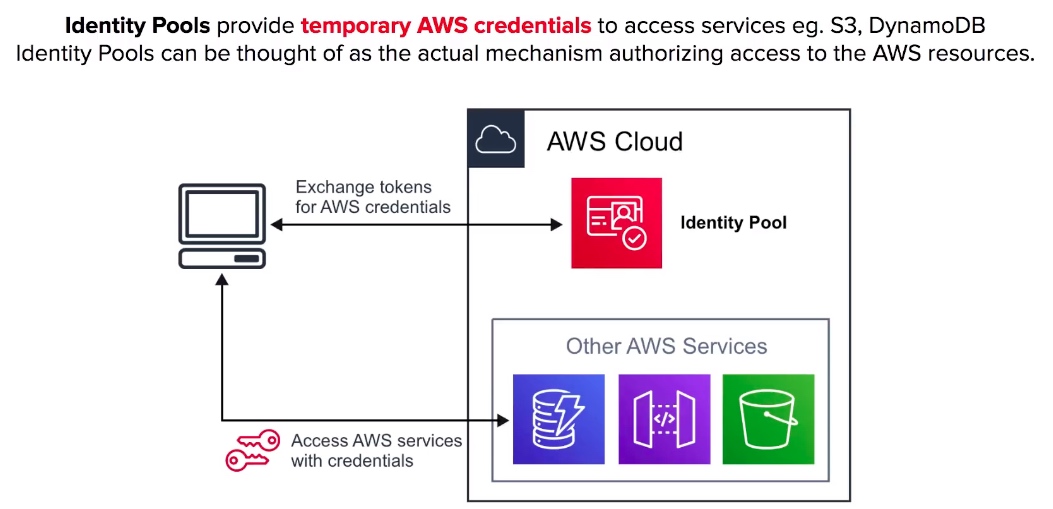
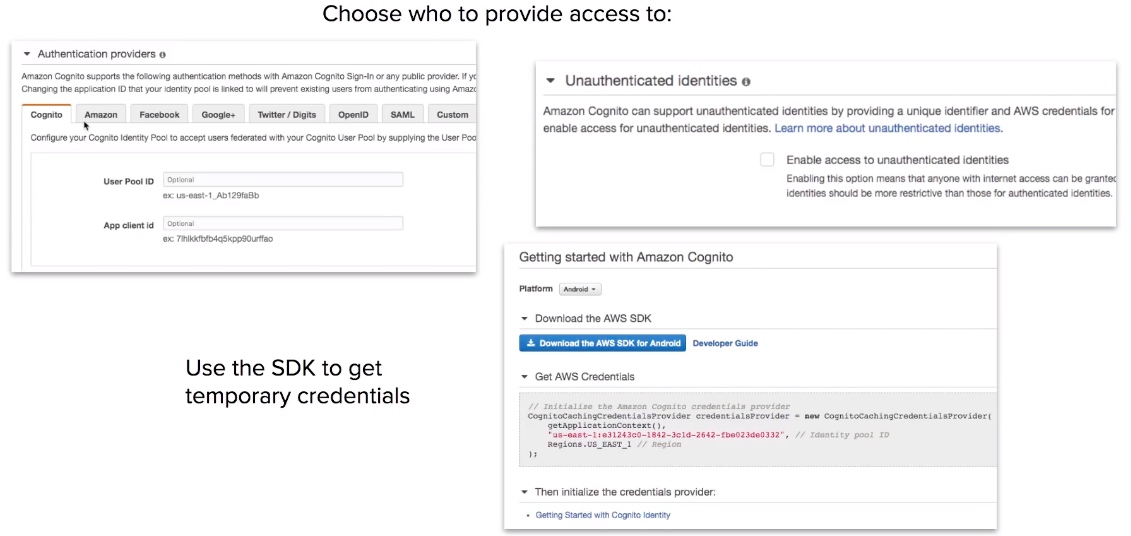
Cognito Identity Pools
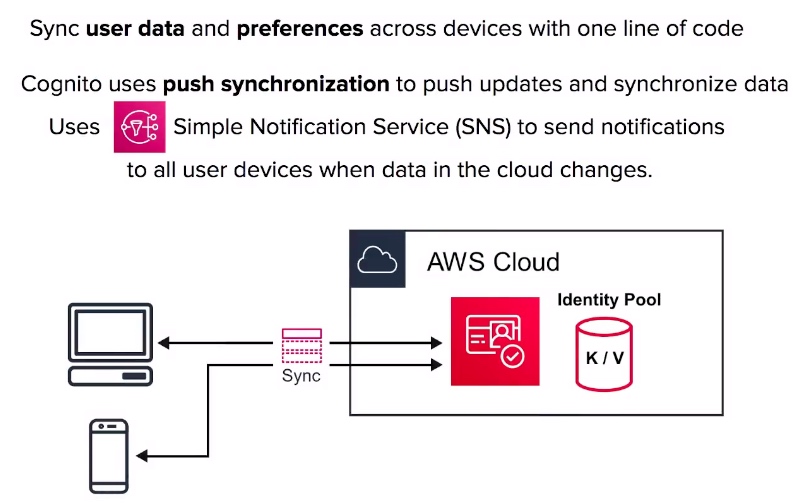
Cognito Sync
Cognito CheatSheet
- Cognito is decentralized managed authentication system. When you need to easily add authentication to your mobile and desktop app think Cognito
- User Pools user directory, allows users to authenticate using OAuth to IpD such as Facebook, Google, Amazon to connect to web-applications. Cognito User Pool is in itself a IpD.
- User Pools use JWTs for to persist authentication.
- Identity Pools provide temporary AWS credentials to access services eg. S3, DynamoDB.
- Cognito Sync can sync user data and preferences across devices with one line of code. (powered by SNS)
- Web Identity Federation exchange identity and security information between an identity provider (ldP) and an application.
- Identity Provider (IdP) a trusted provider of your user identity that lets you use authenticate to access other services. eg. Facebook, Twitter, Google, Amazon.
- OIDC is a type of Identity Provider which uses Oauth.
- SAML is a type of Identity Provider which is used for Single Sign-on.
AWS CLI & SDK
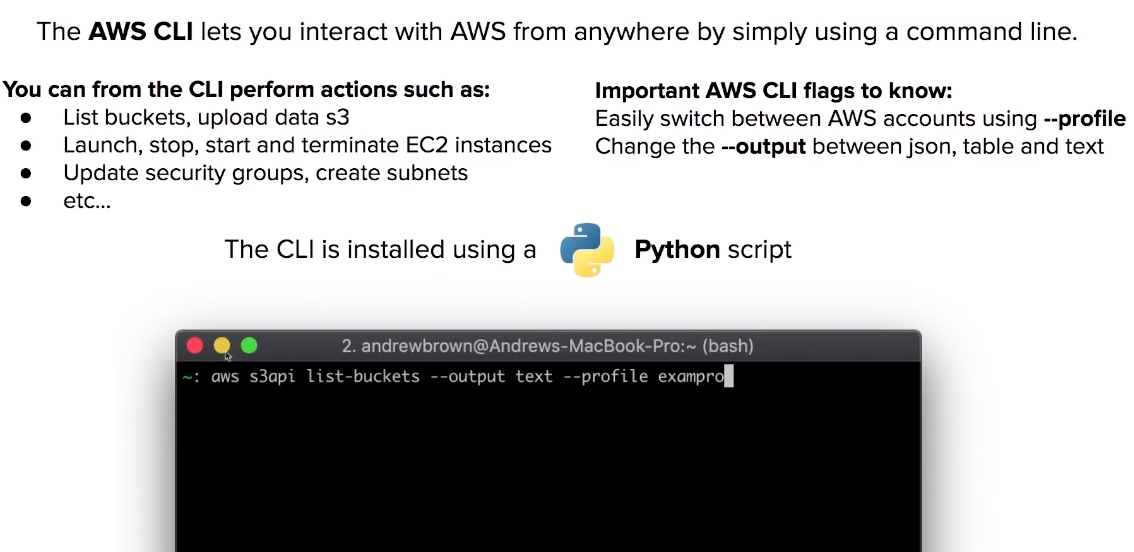
AWS Command line interface
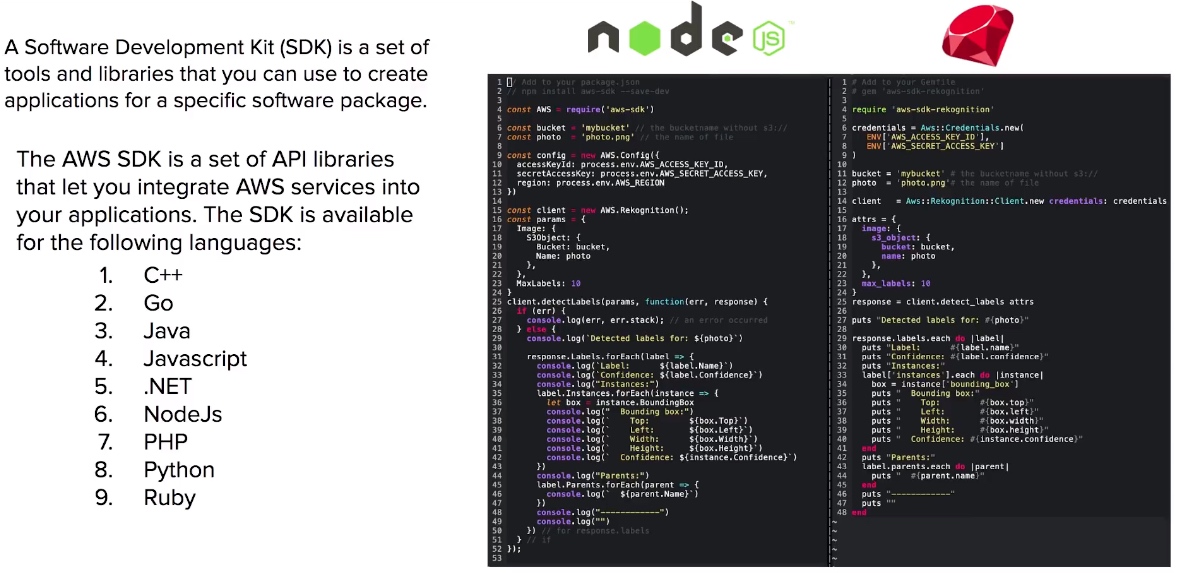
AWS Software Development Kit (SDK)
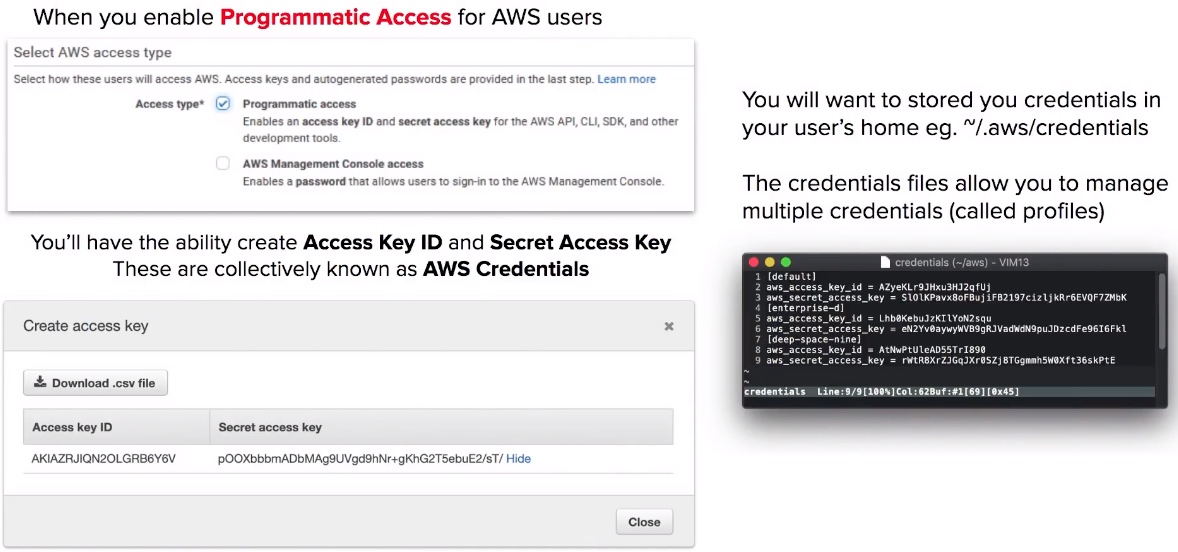
Programmatic Access - Access Key and Secret
AWS CLI & SDK CheatSheet
- CLI stands for Command Line Interface.
- SDK stands for Software Development Kit.
- The AWS CLI lets you interact with AWS from anywhere by simply using a command line.
- The AWS SDK is a set of API libraries that let you integrate AWS services into your applications.
- Programmatic Access must be enabled per user via the IAM console to use CLI or SDK.
- aws configure command used to setup your AWS credentials for the CLI.
- The CLI is installed via a Python script.
- Credentials get stored in a plain text file. (whenever possible use roles instead of AWS credentials)
- The SDK is available for the following programming languages
- GO
- Java
- Javascript
- .NET
- NodeJs
- Python
- Ruby